WHAT WE DO
Attacks are targeting important business data and information that has accounted for more than 80%. Hackers have gradually shifted from destructive purpose trends to financial purposes.
Applications must meet basic safety and security needs. That's why you need a security solution for the source code.
SKG brings you a solution to ensure information security in the source code not only at a reasonable cost, but also eliminates the fear of information security in your application.
TOP 9 SECURITY RISKS
1. Injection
2. Broken Authentication
3. Sensitive Data Exposure
4. XML External Entities
5. Broken Access Control
6. Security Misconfiguration
7. Cross-site Scripting
8. Using Components with Known Vulerabilities
9. Insufficient logging and monitoring
TYPICAL PROJECTS
MIOVI - INFORMATION SECURITY ASSESSMENT FOR INVESTMENT FUND MANAGEMENT SYSTEM
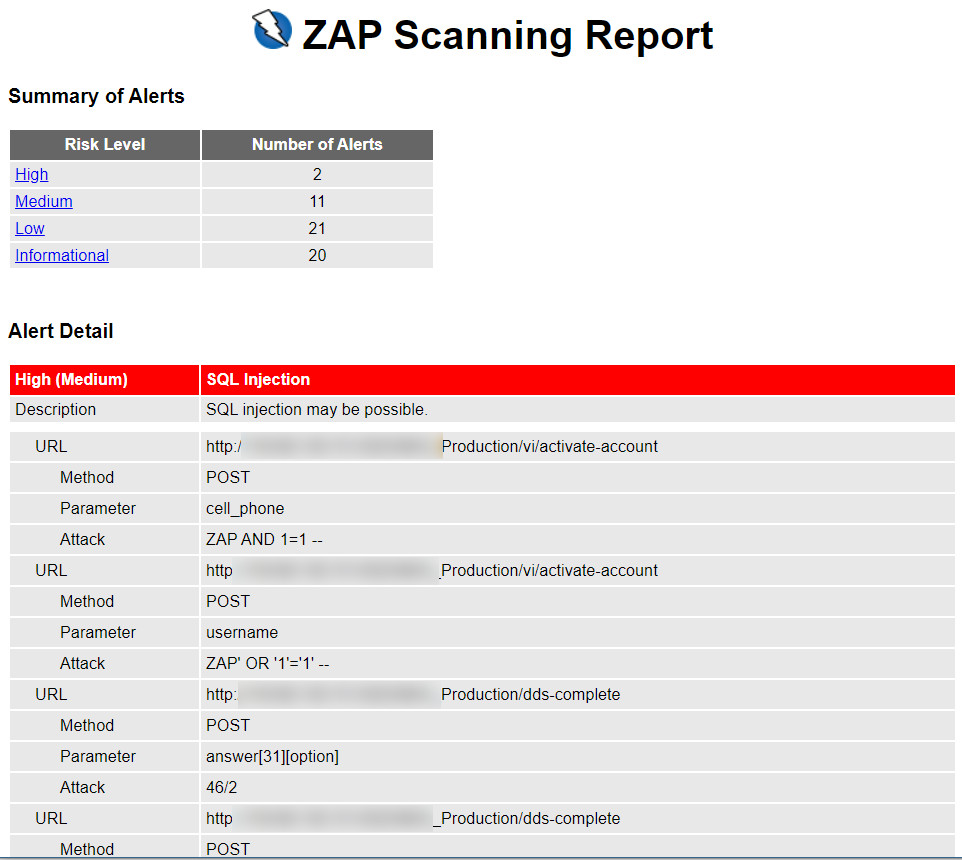
MIOVI is a security assessment project on source code and the handling of security vulnerabilities that SKG makes to an investment fund management company.
SKG uses the OWASP ZAP tool to check for security vulnerabilities in source code. The evaluation results show 34 security holes, of which 4 are very serious.
SKG has come up with a solution to solve security vulnerabilities, ensure a safe operation system, eliminate big information security risks for customers.
Main security vulnerabilities :
- Access financial information without authentication
Access a list of all investment transactions
Access to the entire investor list
Full access to the system’.pdf documents

